Are you interested in statistics? Most people are, and here are some unusual ones that we’ve uncovered: approximately every 39 seconds, people upload about 48 hours of YouTube videos, Tweet 184,000 times on Twitter, submit 1,640,000 posts on Facebook, drink a little more than 2,032 cups of coffee – and eat 104 bananas. Oh – and one computer is hacked in the same amount of time, every 39 seconds, every day of the year. In fact, according to the National Security Agency, there are 300 million hacking attempts every day.
That is good news for social media and coffee companies, but it’s certainly not good news for computer users and businesses that are worried about their account security. To be clear, it isn’t only the large companies like Target, Experian, Microsoft and Facebook, who have suffered data breaches. The fact is, 43% of hacker attacks go after small businesses, not only stealing their clients’ personal and financial information, but locking up their data until a ransom is paid to unlock it.
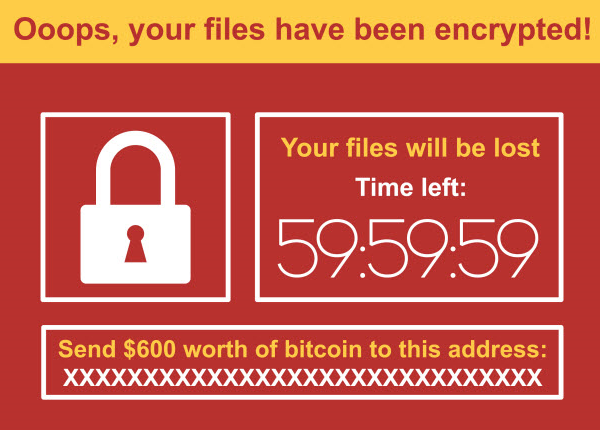
Ransomware is one of the fastest-growing cybercrimes, hitting everyone from hospitals and city governments to beef producers and gas pipeline operators. The ransom is very costly, and is passed on to consumers.
At other times, hackers place malware after hacking into a computer or system, which can give the cybercrook complete control of the computer, along with access to anything they want in the database.
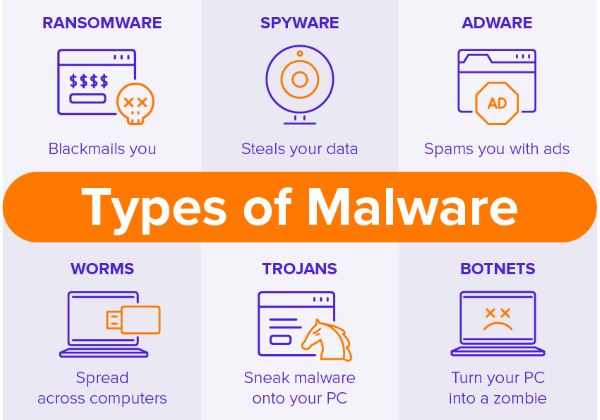
Hacking and Cracking: Cyberthieves at Work
If you had to guess what the weakest link is in account security, would your answer be the IT department? A weak firewall? Or, would it be weak and misused passwords? If you guessed passwords, pat yourself on the back. Because the biggest entry to hacking attacks are passwords. They’re either not strong enough or properly used, and once a hacker gets into your computer and gains access to all of the data that’s stored online, it’s going to be a long, costly battle to restore systems – and customer confidence.
Here’s something else to consider: most hacking and data breaches aren’t discovered until a lot of time passes – as long as months in many instances. That’s a long time to do financial damage to a company or individual.

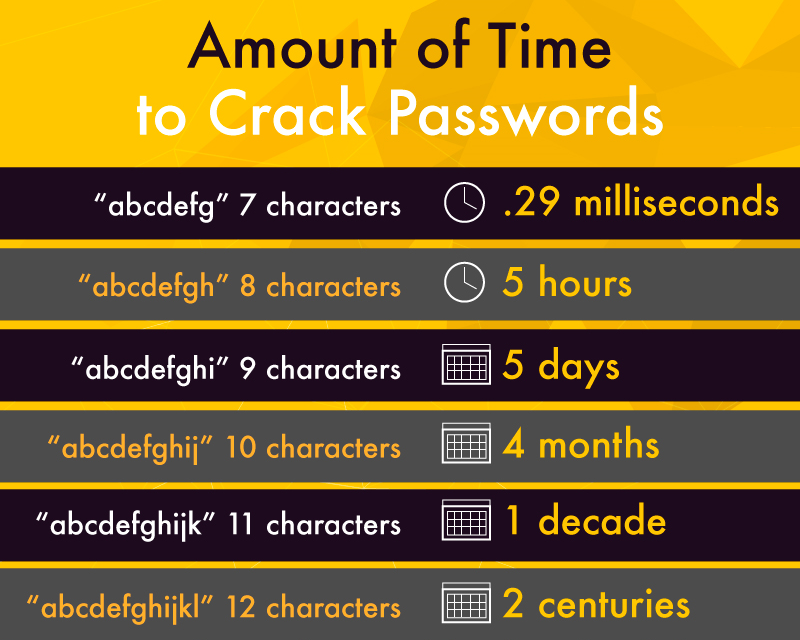
So, what exactly is a strong password? According to IT experts, a strong password should be 12 characters long, and include letters, numbers and symbols.
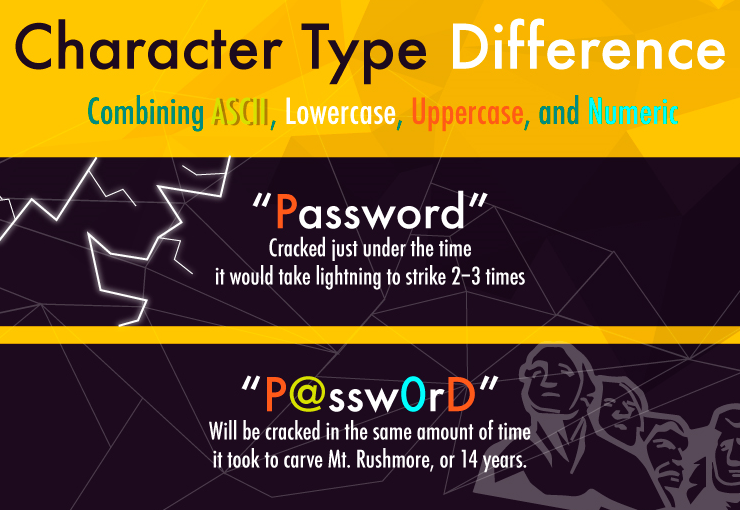
In addition, you should have a different password for every single account you log into – no exceptions, because once a hacker has your password from one account, they’ll try it on every other account you have.
Passwords are often sold on the dark web, but most hackers lean toward “cracking” them. One of the ways they do this is via “credential stuffing,” where cyberthieves acquire a lot of stolen passwords and then use automated methods of trying to break into various accounts. Because many people use the same password over and over again, the hacker will gain access to multiple accounts, until they hit “paydirt” and break into accounts that have sensitive information needed for identity theft.
Another tactic is the age-old phishing email, only now it has a new twist thanks to spoofing. The cyberthief sends out emails that look real, with links to login pages that take the victim to websites that also look real. The only problem is they’re not real – they’re phony, and their only purpose is to capture a person’s password, username or other data that will allow them to cause more havoc.
Finally, hackers like to “guess” your password using sophisticated algorithms, and can even automate this process. They would have to make multiple attempts, however, unless they know how many characters your password contains. If you have a strong password, you’d make their lives miserable, because it would take forever to guess your password, even if they had immense computing power. Plus, if you use 2-factor authentication, they couldn’t get in even when they were lucky enough to guess your password.
Keeping Your Account Secure
Ok, what’s the best way to manage all of the strong passwords the experts recommend, along with having a strong password for every one of your accounts? Use a password manager! They not only generate strong passwords, they remember them for you and use them when required. Some of the top password managers include PasswordBoss, Bitwarden and LastPass.
Some browsers, like Google Chrome and Microsoft Edge, for example, also have their own built-in password managers. They’re also quite effective, and if you use a secure computer in a location where outsiders have access to your device, you can let them automatically save and place your passwords on selected sites that you choose. This really speeds up the login process, but they’re not as safe and secure as password managers. The risk is that if someone gets your computer’s main login password, they would be able to see all of the other stored passwords.
Another issue with storing your passwords is keeping them in a safe place. Never put them in your computer’s document file with a listing of “passwords”. That’s the first place a cybercrook will look at. The best way to keep a copy of all of your strong passwords is to write them down or print them out, and then store that information in a safe, secure place.
Here’s a final word of caution: don’t change your passwords too frequently. It used to be that the IT folks would recommend continually changing your passwords, like once a month, just to be “safe”. Surprisingly, they found that this task made people choose passwords that were easier to come up with and implement. So now the recommendation is if you have a strong password, use it until you believe your password has been compromised.
By following the information and recommendations listed above, you’ll ensure that you have strong passwords and your account security will be rock solid.





